Which Of The Following Is A Valid Fundamental Security Principle 71+ Pages Solution [1.2mb] - Updated 2021
65+ pages which of the following is a valid fundamental security principle 800kb. None of the above Ans. This fundamental security principle defines that the security measures implemented in the software and the hardware must be simple and small. This would ease the testers to test the security measures thoroughly. Check also: following and understand more manual guide in which of the following is a valid fundamental security principle A late 1990s fighter jet project required dozens of separately.
Which of the following is a valid fundamental security principle. The author of a series of threatening e-mails consistently uses im instead of Im This.

Airbnb Booking Assistant Travel Agent Concept Travel Agent App Design Inspiration Airbnb App
| Title: Airbnb Booking Assistant Travel Agent Concept Travel Agent App Design Inspiration Airbnb App |
| Format: PDF |
| Number of Pages: 287 pages Which Of The Following Is A Valid Fundamental Security Principle |
| Publication Date: December 2017 |
| File Size: 1.35mb |
| Read Airbnb Booking Assistant Travel Agent Concept Travel Agent App Design Inspiration Airbnb App |
 |
If the designed security mechanism is complex then it is likely that the tester would get a chance to exploit the weakness in the design.

Choose all that apply a. Which of the following is a valid fundamental security principle. Locards Exchange Principle B. Choose all that apply a. Establish policies that would secure the organizations security perimeter a secure baseline and processes should be developed for ensuring configuration management. Which of the following is a valid fundamental security principle.

Giuliano Liguori Ingliguori Twitter Data Protection Impact Assessment Cyber Security Awareness Information Security Governance
| Title: Giuliano Liguori Ingliguori Twitter Data Protection Impact Assessment Cyber Security Awareness Information Security Governance |
| Format: PDF |
| Number of Pages: 271 pages Which Of The Following Is A Valid Fundamental Security Principle |
| Publication Date: October 2019 |
| File Size: 2.1mb |
| Read Giuliano Liguori Ingliguori Twitter Data Protection Impact Assessment Cyber Security Awareness Information Security Governance |
 |

What Is The Rsi Indicator Binance Academy In 2021 Technical Analysis Indicators Technical Analysis Rsi
| Title: What Is The Rsi Indicator Binance Academy In 2021 Technical Analysis Indicators Technical Analysis Rsi |
| Format: eBook |
| Number of Pages: 275 pages Which Of The Following Is A Valid Fundamental Security Principle |
| Publication Date: August 2021 |
| File Size: 1.4mb |
| Read What Is The Rsi Indicator Binance Academy In 2021 Technical Analysis Indicators Technical Analysis Rsi |
 |

On Acit Institute
| Title: On Acit Institute |
| Format: eBook |
| Number of Pages: 343 pages Which Of The Following Is A Valid Fundamental Security Principle |
| Publication Date: May 2020 |
| File Size: 3mb |
| Read On Acit Institute |
 |

What Is Puter Work Security Work Security Is Any Process Or Activity Which Is Desig Puter Work Security Puter Work Work Security
| Title: What Is Puter Work Security Work Security Is Any Process Or Activity Which Is Desig Puter Work Security Puter Work Work Security |
| Format: eBook |
| Number of Pages: 289 pages Which Of The Following Is A Valid Fundamental Security Principle |
| Publication Date: January 2017 |
| File Size: 1.2mb |
| Read What Is Puter Work Security Work Security Is Any Process Or Activity Which Is Desig Puter Work Security Puter Work Work Security |
 |

Possibly Boring But Very Important Post The European Union S General Data Protect Master Data Management General Data Protection Regulation Mind Map Examples
| Title: Possibly Boring But Very Important Post The European Union S General Data Protect Master Data Management General Data Protection Regulation Mind Map Examples |
| Format: ePub Book |
| Number of Pages: 182 pages Which Of The Following Is A Valid Fundamental Security Principle |
| Publication Date: July 2019 |
| File Size: 1.35mb |
| Read Possibly Boring But Very Important Post The European Union S General Data Protect Master Data Management General Data Protection Regulation Mind Map Examples |
 |
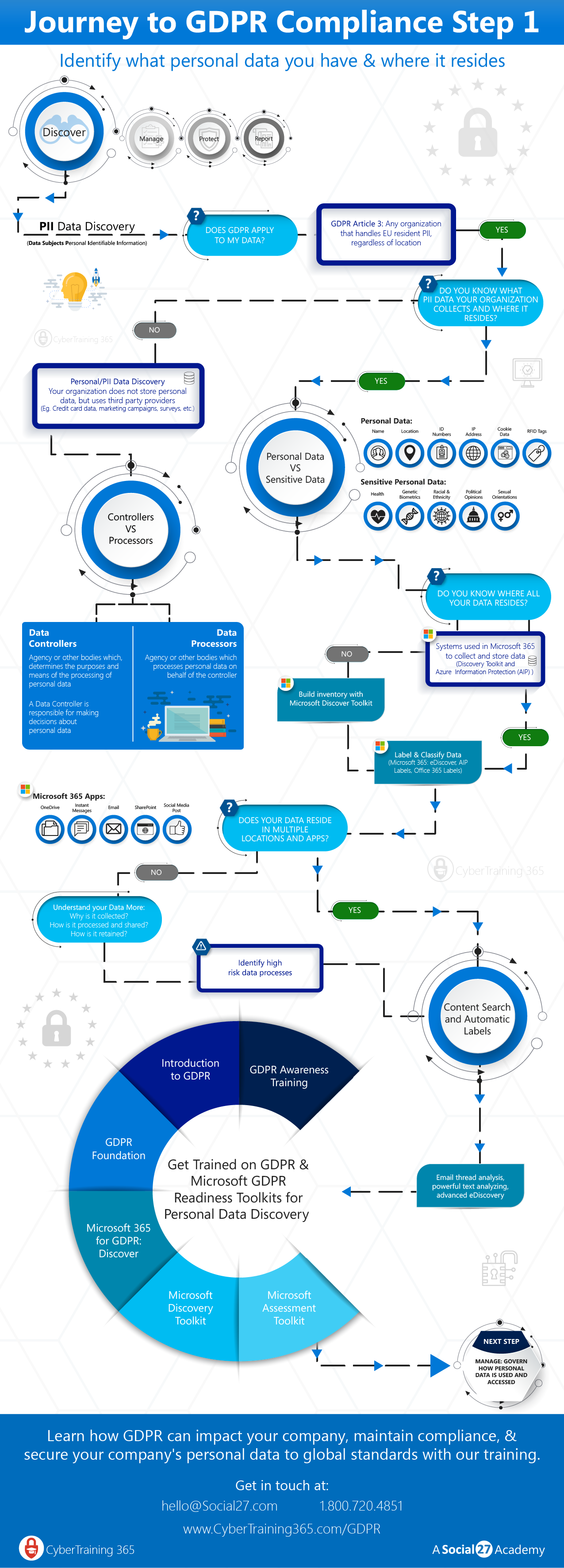
S Key4biz It Wp Content Uploads 2018 04 Gdpr Step 1 Discover 022818 01 Png
| Title: S Key4biz It Wp Content Uploads 2018 04 Gdpr Step 1 Discover 022818 01 Png |
| Format: eBook |
| Number of Pages: 253 pages Which Of The Following Is A Valid Fundamental Security Principle |
| Publication Date: January 2018 |
| File Size: 725kb |
| Read S Key4biz It Wp Content Uploads 2018 04 Gdpr Step 1 Discover 022818 01 Png |
 |

Software Testing November 2016 75 25 Pattern Question Paper Question Paper Paper What Is 5
| Title: Software Testing November 2016 75 25 Pattern Question Paper Question Paper Paper What Is 5 |
| Format: PDF |
| Number of Pages: 188 pages Which Of The Following Is A Valid Fundamental Security Principle |
| Publication Date: January 2018 |
| File Size: 6mb |
| Read Software Testing November 2016 75 25 Pattern Question Paper Question Paper Paper What Is 5 |
 |

Clearsettle New Website Design News Website Design Website Design Web Design
| Title: Clearsettle New Website Design News Website Design Website Design Web Design |
| Format: ePub Book |
| Number of Pages: 231 pages Which Of The Following Is A Valid Fundamental Security Principle |
| Publication Date: November 2018 |
| File Size: 3mb |
| Read Clearsettle New Website Design News Website Design Website Design Web Design |
 |

Sociological Diagram Sociological Concepts Social Learning Theory Sociology
| Title: Sociological Diagram Sociological Concepts Social Learning Theory Sociology |
| Format: eBook |
| Number of Pages: 261 pages Which Of The Following Is A Valid Fundamental Security Principle |
| Publication Date: March 2021 |
| File Size: 1.1mb |
| Read Sociological Diagram Sociological Concepts Social Learning Theory Sociology |
 |

On Back To School
| Title: On Back To School |
| Format: PDF |
| Number of Pages: 184 pages Which Of The Following Is A Valid Fundamental Security Principle |
| Publication Date: December 2017 |
| File Size: 1.35mb |
| Read On Back To School |
 |

What Is The Cia Security Triad Confidentiality Integrity Availability Explained Bmc Software Blogs
| Title: What Is The Cia Security Triad Confidentiality Integrity Availability Explained Bmc Software Blogs |
| Format: ePub Book |
| Number of Pages: 219 pages Which Of The Following Is A Valid Fundamental Security Principle |
| Publication Date: July 2019 |
| File Size: 1.4mb |
| Read What Is The Cia Security Triad Confidentiality Integrity Availability Explained Bmc Software Blogs |
 |
2 Which of the following is not a useful control procedure to control access to system outputs. 1 The Trust Services Framework reliability principle that states that users must be able to enter update and retrieve data during agreed-upon times is known as. The simple principle is also true by itself since each secret increases a systems administrative burden.
Here is all you need to know about which of the following is a valid fundamental security principle Insurable interest will be there where the subject-matter should be in such a position that the insured may suffer loss at the time of damage and may gain by its protection. The criminological principle which states that when anyone or anything enters a crime scene heshe takes something of the scene with himher and leaves something of himselfherself behind is. Which of the following is a valid fundamental security principle. Software testing november 2016 75 25 pattern question paper question paper paper what is 5 what is the rsi indicator binance academy in 2021 technical analysis indicators technical analysis rsi what is the cia security triad confidentiality integrity availability explained bmc software blogs clearsettle new website design news website design website design web design sociological diagram sociological concepts social learning theory sociology airbnb booking assistant travel agent concept travel agent app design inspiration airbnb app A security principal is an object in Active Directory to which security can be applied.

Post a Comment
Post a Comment